From protecting sensitive data to ensuring business continuity, our comprehensive services defend against threats, uphold regulatory compliance, and build trust with your customers.
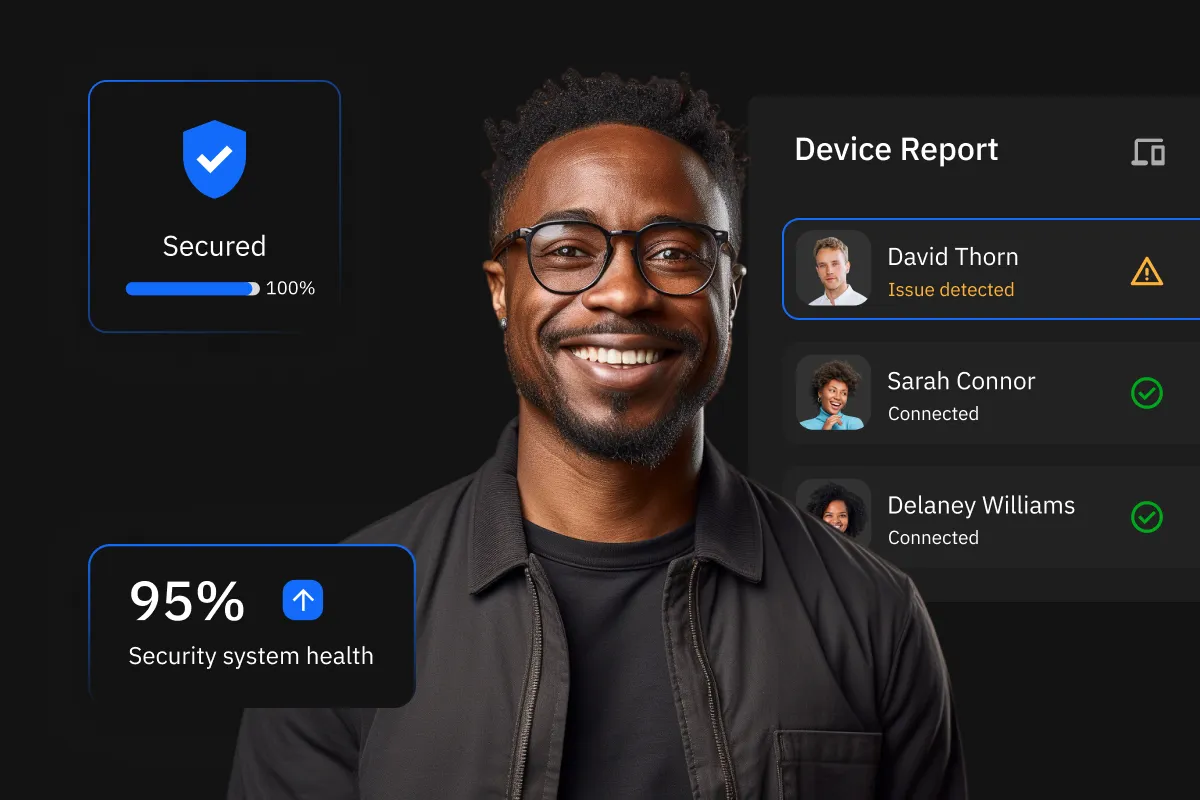
Cybersecurity is paramount for safeguarding sensitive data, ensuring business continuity, defending against threats, and building regulatory compliance and trust with customers. Our services offer comprehensive protection to fortify your digital assets and mitigate risks effectively.
Protects Sensitive Data
Ensure the security of your sensitive data with our robust cybersecurity measures, safeguarding confidentiality and integrity.
Maintains Business Continuity
Our cybersecurity strategies guarantee uninterrupted operations, even in the face of cyber threats, ensuring seamless business continuity.
Defends Against Threats
Stay ahead of cyber threats with our proactive approach, effectively identifying and mitigating malicious attacks to safeguard your digital assets.
Build Trust with Customers
Demonstrate your commitment to data security and privacy, building trust with your customers through our stringent cybersecurity protocols and compliance measures.
Tackle common cybersecurity challenges head-on with proactive solutions

Basic cybersecurity issues

Complex cybersecurity problems

Enterprise challenges
Defend against phishing & malware with education, filters & antivirus. Strengthen passwords with multifactor authentication. Ensure data integrity with reliable backups. Stay proactive with scanning & analytics. Improve access control & secure mobile devices.


Combat APTs with IDS, SIEM, & EDR. Protect against phishing with email filters. Defend from ransomware with antivirus. Manage supply chain risks. Prevent data breaches with DLP. Automate patch management. Develop robust security policies. Secure mobile & remote work with Zero Trust.
Shield your business from DDoS attacks, fortify IoT security, and equip your team to thwart phishing and social engineering attempts. Ensure compliance with regulatory standards, safeguard data integrity, and confidently navigate cloud security challenges.

Risk Assessment and Management
Comprehensive evaluation of the organization's cybersecurity posture to identify vulnerabilities and risks, followed by the development of strategies to manage and mitigate these risks effectively.
Automated Penetration Testing
Simulated cyber attacks against your computer system to check for exploitable vulnerabilities, including testing of applications, networks, and systems to identify and rectify security weaknesses.
Incident Response Planning
Development and implementation of a structured approach for handling security breaches or attacks, minimizing impact, and outlining procedures for recovery and prevention of future incidents.
Security Monitoring and Alerting
Continuous monitoring of network and system activities to detect and alert on suspicious behavior, potential breaches, and security threats in real-time.
Data Protection and Encryption
Implementation of data encryption and other protective measures to safeguard sensitive information from unauthorized access or theft.
Endpoint Protection
Security measures designed to detect, investigate, and respond
to threats on all endpoints, including desktops, laptops, and mobile devices.
If you don't find an answer to your question, please, fill free to contact us
Cybersecurity refers to the practice of protecting computer systems, networks, and data from digital attacks, theft, or damage.
Common cyber threats include malware (such as viruses, worms, and ransomware), phishing attacks, DDoS (Distributed Denial of Service) attacks, insider threats, and social engineering.
A vulnerability assessment is the process of identifying and prioritizing weaknesses in a system. It's important in cybersecurity as it helps organizations understand their security posture and where they need to focus their efforts to strengthen defenses.
Employee training is crucial in cybersecurity as human error is often the weakest link in a security chain. Training helps employees recognize potential threats, understand security protocols, and develop good cybersecurity hygiene practices.
Cybersecurity often involves complying with regulations and standards set by governments, industries, or international bodies. Compliance helps ensure that organizations meet minimum security requirements, protect sensitive data, and mitigate risks effectively. Examples include GDPR (General Data Protection Regulation), PCI DSS (Payment Card Industry Data Security Standard), and HIPAA (Health Insurance Portability and Accountability Act).
We are sorry, but it also happens :( Book a consultation for further information on your specific request.